The Evolving Landscape of IoT Security: The Full Story From 2006 to 2024
Learn the best practices and latest trends in cybersecurity from industry experts.
01 / Blog Article
The Evolving Landscape of IoT Security: The Full Story From 2006 to 2024
Over the last 20 years, many devices have been connected to the internet, enhancing business efficiency. However, by 2006, IoT technology had been exposed to its first cyberattacks. The journey continued in 2014 with significant IoT developments, such as home heat controllers and fitness tracking tools. However, along with progress came increased danger and risk. For example, in 2015, hackers successfully hacked into a Tesla Model S car from a remote location, a concerning development.
The risks continued to escalate, with hackers in 2016 taking control of millions of IoT devices to launch DoS and DDoS attacks. This highlighted the urgent need to enhance the security of these devices. Governments responded by introducing new rules to protect consumers from potentially harmful IoT devices. In 2018, significant steps were taken to secure private data, followed by additional security measures for IoT devices in 2019.
Despite these efforts, IoT security challenges persisted in 2023, indicating the ongoing work required to safeguard these devices.
In this article, we will explore strategies to secure business IoT devices from hackers. We will delve into major hacker attacks, the vulnerabilities of these devices, and the challenges of ensuring their security.
Major IoT Cyberattacks Worldwide
Hackers can easily identify vulnerable IoT devices using tools like Shodan. As IoT devices become more advanced, the risks associated with them also increase. IoT devices can be exploited for spam, phishing emails, and large-scale DDoS attacks that can disrupt websites. Surprisingly, even seemingly harmless devices like washing machines can be used to steal data.
For instance, a user named Johnny discovered that his LG washing machine was sending over 150 megabytes of data every hour, indicating a potential security breach.
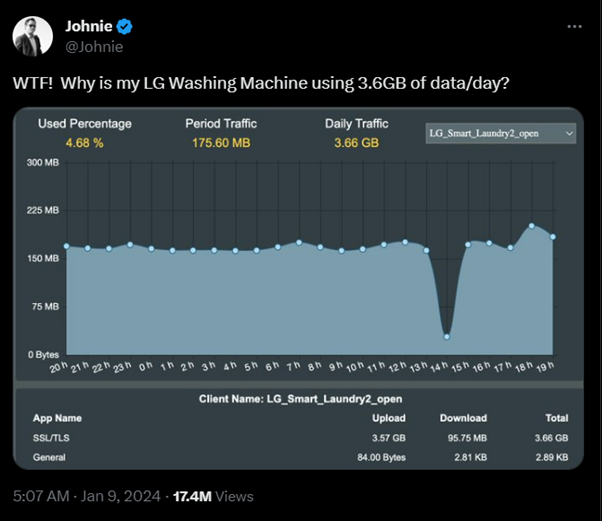
Similarly, electric toothbrushes were found to be susceptible to cyberattacks, as reported by Aargauer magazine in January of this year.
In 2021, Verkada, a company that manufactures security cameras, fell victim to cyberattacks. Hackers gained access to live feeds from 150,000 cameras in locations such as clinics and schools, highlighting the potential security risks associated with IoT devices.
In another incident in 2017, hackers infiltrated a casino in North America through a Wi-Fi-connected fish tank thermometer. They accessed sensitive financial information after first compromising the high-roller database through the thermometer.
One of the most significant IoT attacks occurred in 2016 when the Mirai botnet targeted numerous small web devices like cameras and routers for a massive DDoS attack. This attack caused many websites and online services to crash, underscoring the importance of securing IoT devices.
Understanding IoT Devices
An IoT device refers to any device that can connect to the internet, excluding traditional computers. These devices require maintenance both internally (e.g. software updates) and externally (e.g. communication with other devices).
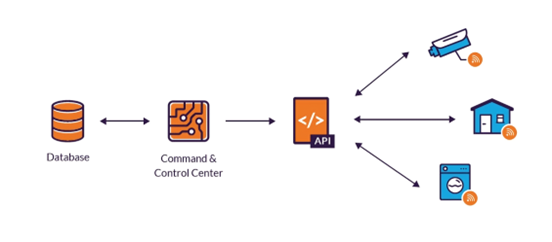
IoT devices rely on a command and control (C&C) center to manage operations such as updates and task performance. They also communicate with each other through an application programming interface (API) to share information and sometimes control one another.
However, C&C centers and APIs have vulnerabilities, including unpatched software, vulnerable APIs, weak authentication, and unencrypted traffic, which can be exploited by hackers.
Businesses often implement standard security measures for computers but may overlook the unique vulnerabilities of IoT devices. Without adequate security measures, IoT devices can be compromised, leading to data theft and system malfunctions.
Safety teams in the IoT industry face several challenges, including:
- Tracking and managing all IoT devices on the network.
- Handling the large volume of data generated by IoT devices.
- Managing IoT devices across different departments within a company.
The Most Vulnerable IoT Devices
Many IoT attacks exploit vulnerabilities in devices connected to the internet. Once hackers gain access to one device, they can escalate their privileges and access other devices on the same network. Common tactics used in IoT attacks include network scans and password attacks.
As shown in the figure below, certain IoT devices are particularly vulnerable to attacks.
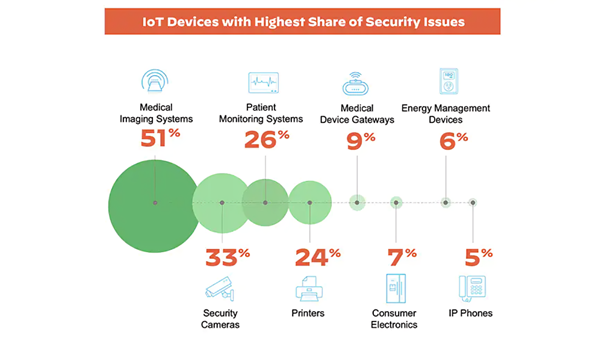
Top IoT Security Threats
Old attack methods that IT security typically mitigates are still prevalent in IoT, alongside new tactics like peer-to-peer communication and self-spreading malware designed for IoT devices. These new tactics often target outdated communication protocols to disrupt business operations.
Password attacks, facilitated by the prevalence of easily guessable passwords on IoT devices, and network scans are among the most commonly used tactics, as illustrated in the chart below.
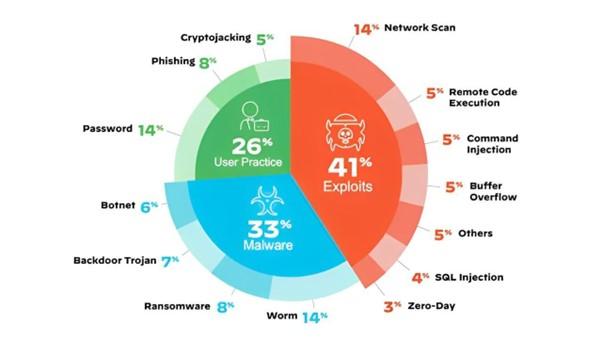
Protecting IoT Devices: Guidelines and Best Practices
While no single group leads in protecting IoT devices from online threats, some initiatives have been taken to enhance their security. For example, in 2020, the National Institute of Standards and Technology (NIST) launched the NIST Cybersecurity for IoT program to promote global innovation through simple rules and advice.
The NIST Cybersecurity Framework (CSF) version 2.0 published on February 26th 2024, provides guidelines for organizations to protect their critical data and systems. It consists of six main domains:
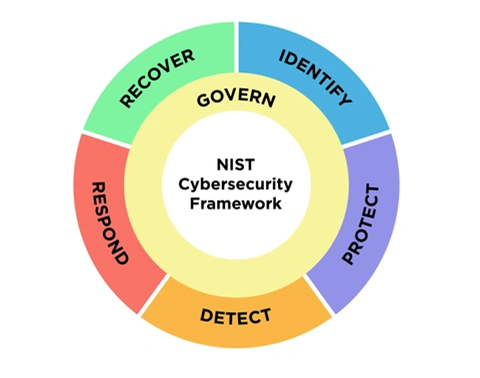
- GOVERN (GV): Establishes and communicates the organization’s cybersecurity strategy for IoT, defining roles and responsibilities and overseeing its implementation.
- IDENTIFY (ID): Figure out what IoT devices you have and what risks they might have. You need to know what kind of data the devices collect and how they can be affected by cyberattacks.
- PROTECT (PR): Use safety steps to protect your network from dangers. This can mean setting up firewalls, using hard-to-guess passwords, and keeping data secret.
- RESPOND (RS): Have a strategy ready for when cyberattacks hit. This should cover how to find and fix broken devices and who to tell about the issue.
- RESPOND (RS):Have a strategy ready for when cyberattacks hit. This should cover how to find and fix broken devices and who to tell about the issue.
- RECOVER (RC): Plan for getting things back to normal after a cyberattack. This may involve repairing devices and checking that everything works right again.
Other best practices for IoT security include:
- Sharing information about risks with others.
- Regularly updating security tactics.
- Being prepared for new threats.
Securing IoT devices is crucial to protect against cyber threats. By following guidelines such as the NIST Cybersecurity Framework and adopting best practices, organizations can enhance the security of their IoT devices and safeguard against potential attacks.

Protect your business with Paratus
Ready to get started? Fill out the form below and we'll get back to you in no time!

risk decrease